Securing customer data is no longer just a technical concern — it’s a core part of building trustworthy banking products. As a product owner, you’re likely to encounter conversations about cryptographic techniques — terms like encoding, hashing, encryption, digital signing, and authentication codes often surface in discussions around security and compliance. However, these concepts can be complex and occasionally overwhelming, especially if you don’t work hands-on with the underlying technology.
This guide breaks down the essentials, helping you understand what each term means, how they differ, and why they matter — so you can navigate security conversations with confidence and clarity.
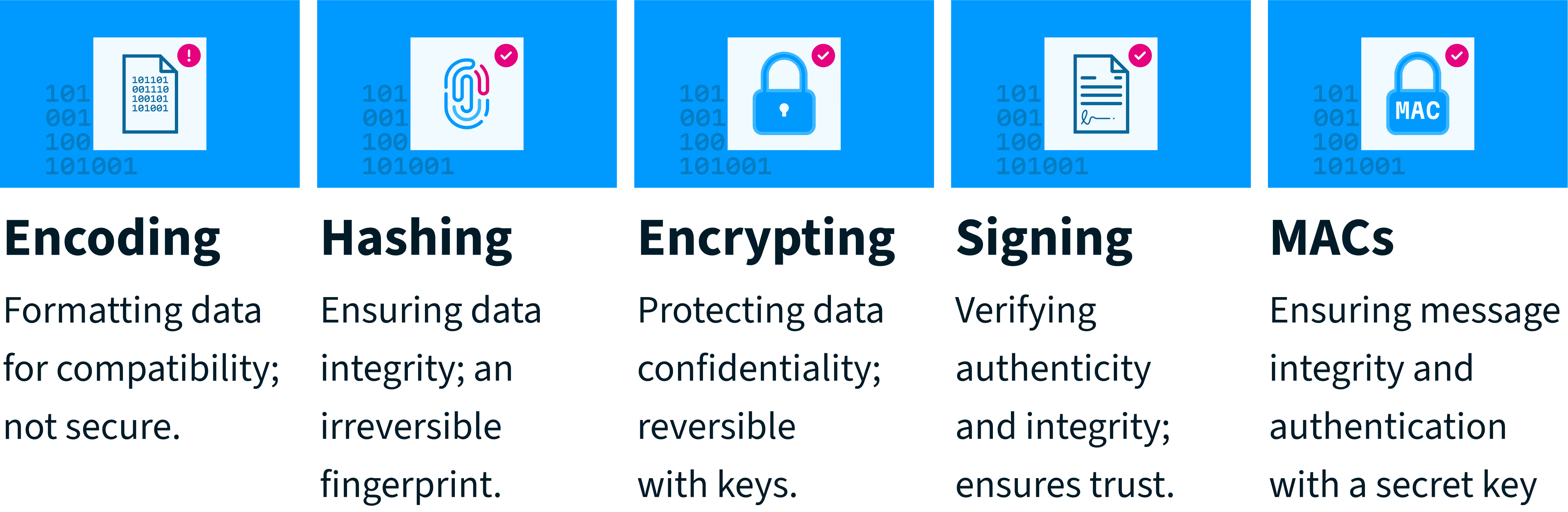
Encoding: Formatting, Not Security
Encoding is essentially about formatting data so it can be transmitted or stored. It transforms data into a more suitable format using schemes like Base64 or Base16 (hexadecimal). While it is not always easy to read the encoded content, encoding itself doesn't provide any security; anyone with the appropriate decoder can effortlessly revert the data to its original readable form.
Example: Converting email attachments into Base64 to ensure they arrive intact.
Important: Encoding does not protect data privacy or prevent unauthorized access.
Hashing: Unique Data Fingerprints
Hashing creates a unique, fixed-size string of characters from data using algorithms like SHA-512. Think of it as generating a fingerprint that is unique to the data and irreversible. While a given piece of data always results in the same hash value, if the data changes, even slightly, the hash value changes significantly.
Example: Password storage — banks store hashes instead of passwords, enhancing security.
Important: Strong hashes can't be reversed to reveal the original data.
Encryption: Protecting Data with Keys
Encryption is about confidentiality. It converts readable data (plaintext) into unreadable data (ciphertext) using cryptographic keys. Only authorized individuals with the correct decryption key can convert it back to plaintext.
Encryption can be categorized into two main types:
- Symmetric Encryption: Uses the same secret key for both encryption and decryption. It is fast and suitable for encrypting large amounts of data. However, if the secret key is leaked by either party, all encrypted data is compromised. The most commonly known algorithm for symmetric encryption is AES (Advanced Encryption Standard).
- Asymmetric Encryption: Uses a pair of keys — a public key (used by the sender of the secret message) and a private key (used by the receiver to decrypt the original message). While slower than symmetric encryption, it provides enhanced security as only the private key needs to be protected. Legacy algorithms for asymmetric encryption, such as RSA or ECIES (Elliptic Curve Integrated Encryption Scheme), are being replaced by stronger, quantum-safe alternatives, such as CRYSTALS-Kyber.
Example: Securing internet banking communication with TLS/SSL encryption ensures no malicious actor can eavesdrop.
Important: Encryption can be reversed (decrypted), but only by those holding the correct key.
Digital Signing: Authenticity and Trust
Digital signatures verify the authenticity and integrity of digital information. They prove who sent or approved the information and ensure it hasn’t been altered since signing. The party that wants to provide the proof uses its private key to add a digital signature to the information. The party that wants to verify the proof later uses the public key to verify that the proof matches the original information.
Legacy algorithms for digital signatures, such as RSA or ECDSA (Elliptic Curve Digital Signature Algorithm), are being replaced by stronger, quantum-safe alternatives, such as CRYSTALS-Dilithium.
Example: Signing electronic loan agreements or authenticating users with passkeys (FIDO2).
Important: Digital signatures authenticate the sender and ensure the content has not changed.
MACs (Message Authentication Codes): Integrity and Authentication
Like Digital Signatures, Message Authentication Codes (MACs) verify a message's authenticity and integrity, ensuring the message content hasn't been altered and confirming that the sender possesses the correct key.
Unlike digital signatures, however, MACs use a shared secret key. As a result, they do not provide a non-repudiation property. Any party that possesses the secret key, sender or receiver, could have computed the MAC value.
Algorithms for MACs include KMAC (Keccak Message Authentication Code) or HMAC (Hash-Based Message Authentication Code).
Example: Verifying integrity and authenticity in payment transactions using an authentication code defined in PSD2’s Strong Customer Authentication (SCA).
Important: MACs provide authenticity and integrity but not non-repudiation.
What This Means for Your Role in Security
Understanding these concepts will help you engage more effectively in security discussions, clearly articulate requirements, and ensure the right security measures are in place for your banking products. A solid grasp of cryptographic principles ensures that data protection isn't just a checkbox — it's a well-informed strategy.
Quick Reference Summary:


.webp)