We recently told you about a handful of current threats facing mobile banking users. In that post, we mentioned multi accounting, which is the act of purposefully creating multiple accounts in order to abuse a system. Multi accounting attacks on banking steal victims’ credentials and attackers pair victim’s accounts to mobile banking on their devices. A surefire way to protect against this type of attack is to implement a more thorough identity verification using a personal ID scan and server-side face biometrics.
Multi accounting attacks aren’t the only type of threat that can be avoided with the use of proper identity verification. Facial authentication is one of the good ways to verify one’s identity with a high level of confidence. However, it isn’t a one-size-fits-all solution; there are multiple “levels” of facial authentication that provide corresponding levels of protection.
In order to put the strengths and weaknesses of each type of facial authentication on display, let’s have a look at the two larger dimensions of this biometric authentication method.
Device-Side vs. Server-Side Authentication
What Is Device-Side Authentication?
In device-side authentication, each of the steps of facial authentication — analysis, biometric template creation, storage, and matching — all take place locally on a user’s device.
A good example of technology that makes use of device-side authentication is Face ID, Apple’s facial recognition technology that is widely used by Apple users across the globe.
While Face ID is the right solution for certain situations (like simply unlocking your phone or approving low-risk transactions), it doesn’t cover all the bases in terms of security. In fact, there have been reports of Face ID-related vulnerabilities, which Apple continues to respond to and patch on an ongoing basis. More importantly, Face ID does not truly verify a user's identity when logging in to digital banking or while approving payments. The face enrolled in Face ID is in no way connected to the person that the bank knows — in theory, it can belong to anyone who has added their face in iOS settings.
This being said, it’s worth noting that Face ID at least carries out additional checks to make the local authentication precise. It carries out a liveness check (we’ll explain this term more in a bit) and is attempting to add more advanced checks, such as "attention awareness checks."
What Is Server-Side Authentication?
When applying server-side authentication, a user’s biometric data is entered and centrally stored within a secure server instead of their device. Whenever they attempt to verify their identity using facial biometrics, their biometric sample is sent to the centralized matching engine, where it’s paired up against the data template that was previously stored. When onboarding a new user, the biometric template is usually entered based on prior identity verification. Therefore, server-side biometrics truly verify an actual user’s identity.
In a nutshell, the use of server-side facial biometrics involves more advanced user onboarding and individual biometrics, which ultimately results in heightened security for the end user.
Levels of Facial Authentication Technology
Facial Recognition
This is the simplest — and least secure — form of facial authentication. Facial recognition does exactly what it sounds like: it recognizes one’s face. That being said, facial recognition can fall prey to a number of authentication-related threats, like facial spoofing (more on that below).
Liveness Detection
Due to the way that basic facial recognition works, it can fall prey to facial spoofing attacks. In simple terms, facial spoofing is the act of an attacker using a person’s face (in the form of a photo or video) to pretend to be that person in an effort to trick (and ultimately bypass) facial biometric identification control systems.
One way to make sure these attacks can’t happen is to use facial liveness detection.
Facial liveness detection can be defined as the use of technology to detect the harmless presence and vital signs of a live user, rather than a picture, a fake video, or a mask. This differentiation is made possible by the use of algorithms that analyze biometric data — this is the component that provides security against facial spoofing attacks. Simply put, after a user scans their face, liveness detection technology will verify whether or not the source is coming from a fake representation.
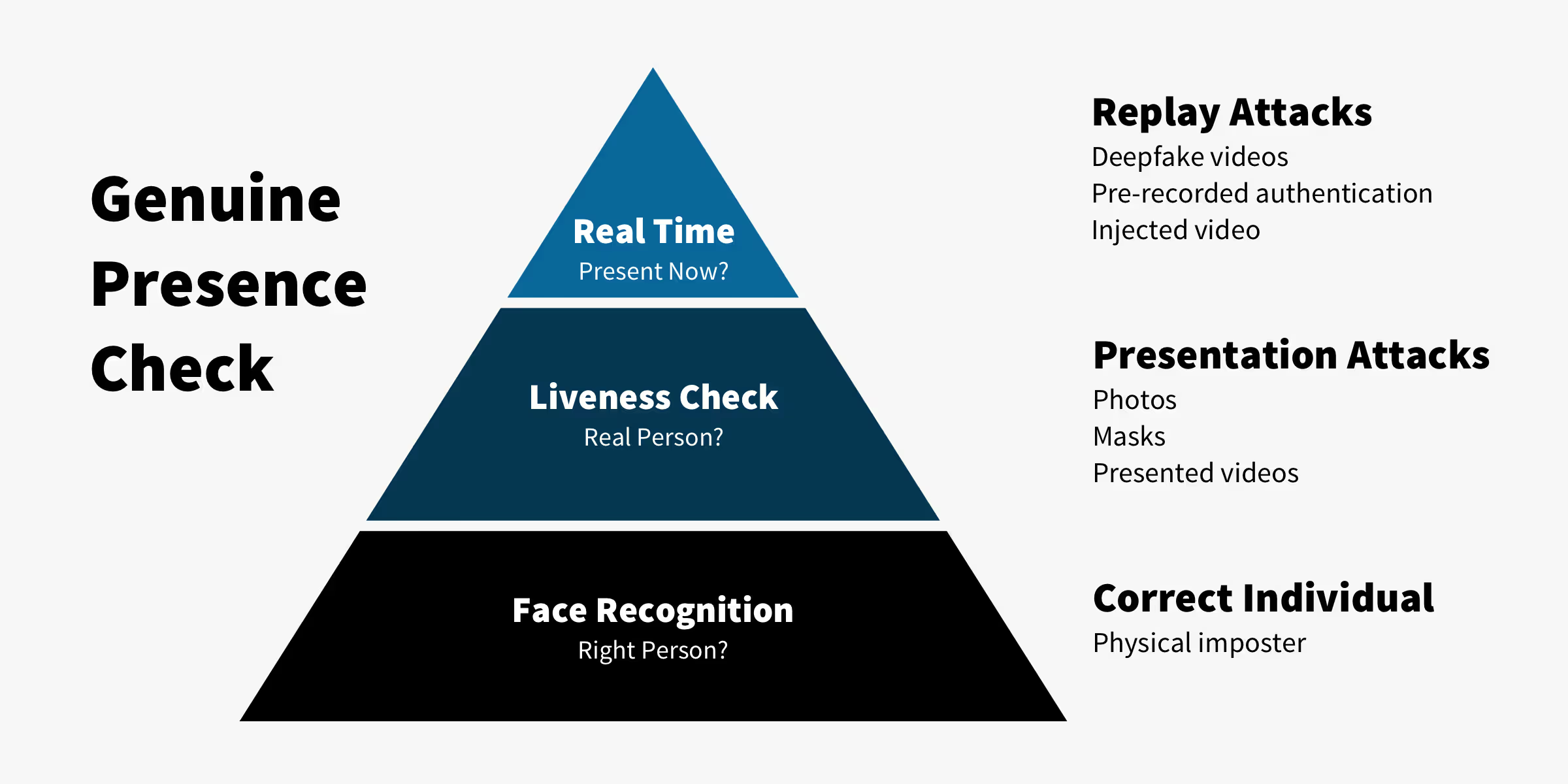
Genuine Presence Check
Genuine presence check is a form of advanced biometric authentication. It incorporates a real-time verification system based on a visual challenge-response using display and camera to authenticate transaction attempts and to verify that the biometric authentication is taking place in real time.
As is shown in the graphic below, this extra step can protect against certain fraudulent verification types like deepfake videos as well as pre-recorded or injected videos (these are also referred to as “tethered attacks”).

How Can Your Business Benefit from Facial Authentication?
As we’ve explored in this post, the various levels of facial authentication each come with their own pros and cons. It’s important that businesses and application developers keep the level of necessary security in mind while crafting and releasing products — and in the case of mobile banking and fintech applications, it almost goes without saying that increased security measures are a must.
Another important note: Making use of multiple biometric measures for authentication (such as a keystroke analysis paired with facial recognition) can help achieve higher biometric performance, since this creates more obstacles for cybercriminals while maintaining a positive user experience. Stay tuned — we will elaborate on these points in a future post.


.webp)