As the world prepares for the quantum computing era, fears of massive slowdowns and performance bottlenecks in authentication systems are common — and understandable. After all, post-quantum cryptographic (PQC) algorithms use significantly larger keys and are more complex than their classical predecessors.
The reality is far less dramatic. When implemented thoughtfully, post-quantum authentication increases infrastructure demands by only about 15% — a manageable margin in most modern environments.
The Big Impact is in Low-Frequency Use Cases
The key distinction lies in which cryptographic components are affected by quantum threats. Asymmetric cryptography — used for key agreement exchanges and digital signatures — is the most vulnerable and thus must be replaced by post-quantum alternatives like ML-KEM and ML-DSA.
These algorithms are computationally heavier and generate larger key material and proofs. However, they are only used in a limited set of operations, such as:
- Authenticator registration
- Symmetric encryption key provisioning
- Digital signature generation and validation
In most authentication systems, these operations are infrequent or occur once per user/device lifecycle.
Symmetric Operations Do Most of the Heavy Lifting
Most real-world authentication flows — logins, transaction approvals, session management — can be safely based on symmetric encryption and message authentication codes (MACs). These cryptographic primitives:
- Are resilient to quantum attacks with minor adjustments (AES-256 instead of AES-128)
- Do not significantly increase processing time
- Do not require significantly large keys or payloads
Because operations based on symmetric cryptography remain compact and fast, authentication systems' day-to-day performance remains virtually unchanged.
Modest Infrastructure Upscale
In an authentication system, post-quantum cryptographic algorithms have an impact on infrastructure, which is surprisingly modest:
- CPU and memory requirements increase by ~15% on average across common authentication use cases. This includes the cost of handling larger keys and performing heavier computations during key exchange or signature verification.
- Database storage needs grow due to larger public keys, digital signatures, and other cryptographic proofs. Systems must account for storing credentials and logs that are noticeably bigger than their pre-quantum counterparts.
- Network overhead may increase slightly when post-quantum keys or artifacts are transmitted during device enrollment or attestation, but even there, the impact is mostly for low-frequency use cases.
All these changes safely remain within the capacity of modern authentication infrastructures, especially those already scaled for high availability and security. Below are some practical statistics from our post-quantum authentication platform:
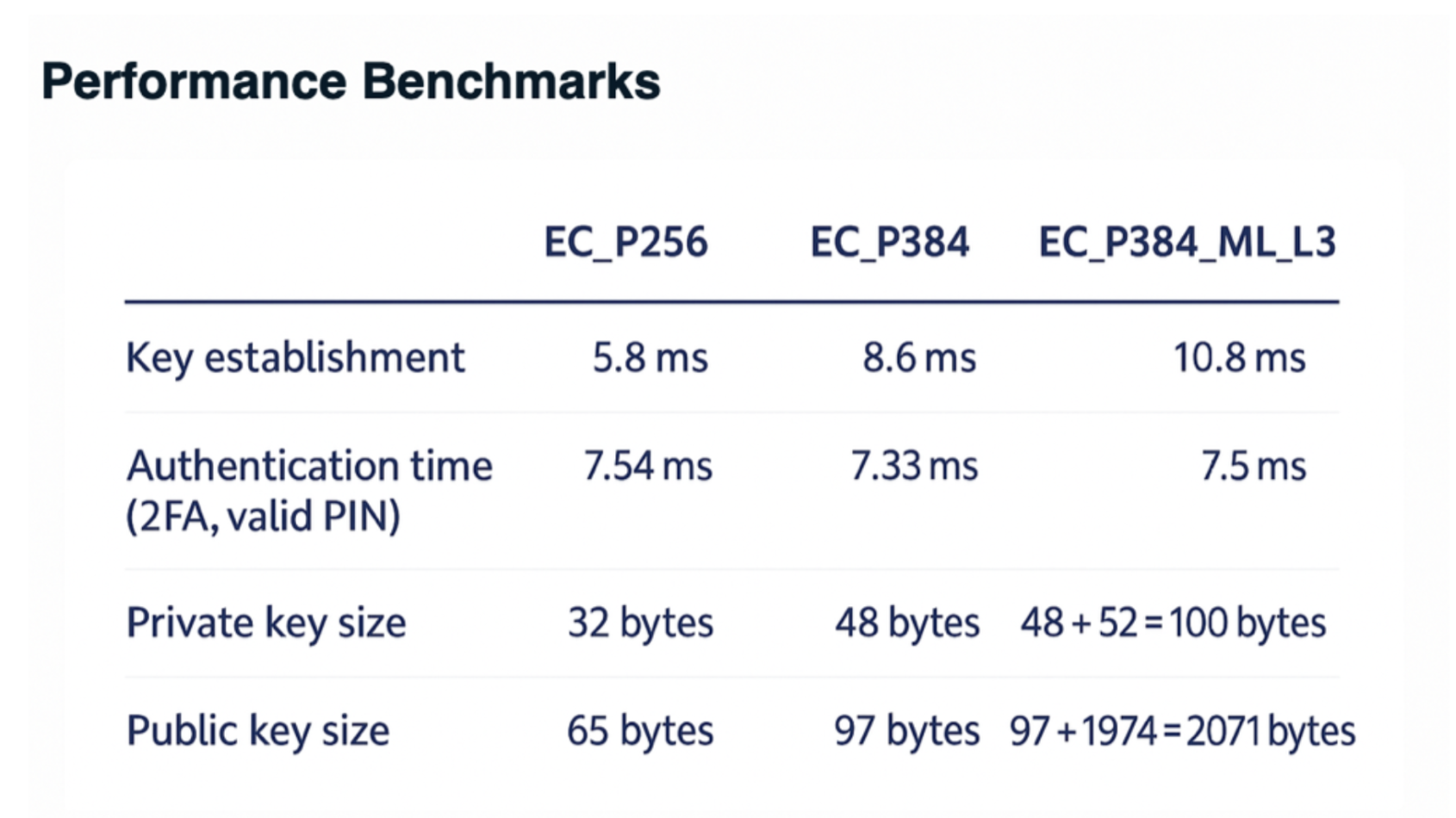
Don’t Fear the Quantum Leap
The shift to post-quantum authentication is not about tearing down what works — it’s about upgrading the right components at the right places. By isolating the use of post-quantum algorithms to the infrequent asymmetric steps, while maintaining efficient symmetric operations for everything else, the infrastructure burden is kept light and predictable.
With a manageable 15% overhead, and growing urgency from regulators and standards bodies, there’s little reason to delay. The future of authentication is quantum-safe — and it scales.
Explore our PQA solution and see the numbers for yourself.


.webp)